AUTH Two Factor Verification #
The Application Detail’s AUTH tab serves as the primary control panel for configuring various application parameters. Within this tab, you can manage two-factor verification, permission settings, associated user meta-data format, invite meta-data format, password requirements, and customized email extensions. The versatility of the CoSync Auth authentication system is empowered by the capabilities offered within the AUTH tab.
As a developer, you often need the added security of two-factor verfication added to your application login process. Don’t worry, CoSync Auth has you covered. The AUTH tab provides three types of two factor verification
- None
- Phone
No Two Factor Verification #
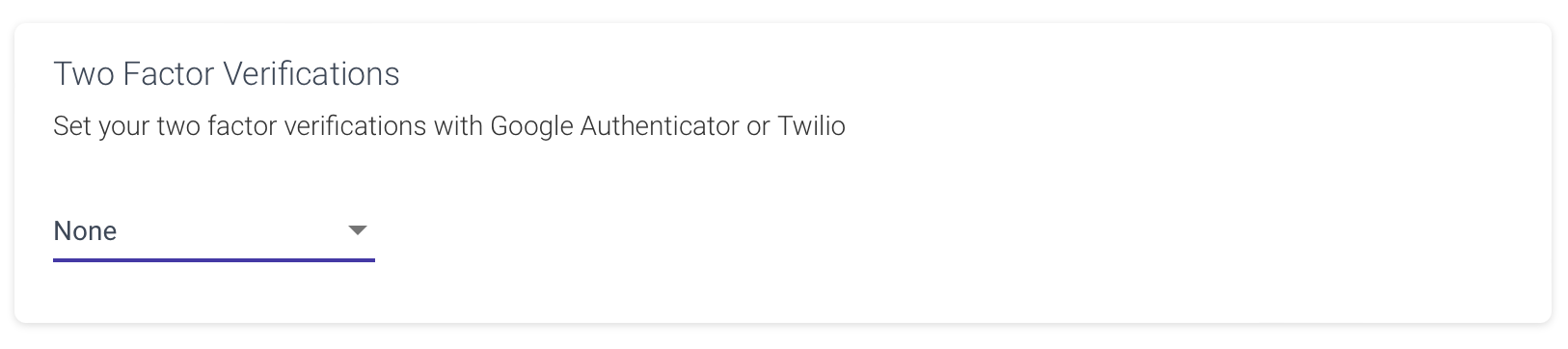
By default, the two-factor verification setting is None, signifying the absence of such verification. In this particular scenario, a user can log in using either their email/password or username/password credentials. Once the provided password matches the associated email or username, the login process proceeds successfully.
Google Two Factor Verification #
Google Verification stands as a preeminent exemplar of two-factor authentication, striking a remarkable balance between security and cost-effectiveness, coming to you free of charge. Its implementation, however, necessitates the installation of the Google Verification app on the user’s mobile device. This authentication system relies on time-based one-time passwords and HMAC-based one-time passwords to validate users accessing software applications.
The login process for sites or services supporting Authenticator and employing two-factor authentication unfolds as follows: The user provides their username and password. The site then quietly computes a concealed six-digit one-time password and prompts the user to input it. Concurrently, the user activates the Authenticator app, autonomously deriving and displaying the identical password, which they dutifully enter, conclusively affirming their identity.
Notably, the potency of this two-factor authentication denies access to malicious intruders relying solely on the knowledge of username and password. To breach a user’s account, assailants must possess the shared secret key or physical access to the device harboring the Authenticator app, affording an admirable layer of protection.
Enabling two-factor authentication with Google is a straightforward process. The user can achieve this by configuring Google as the authentication method, associating it with an application name tailored to the developer’s specific needs, such as ‘Toto’.
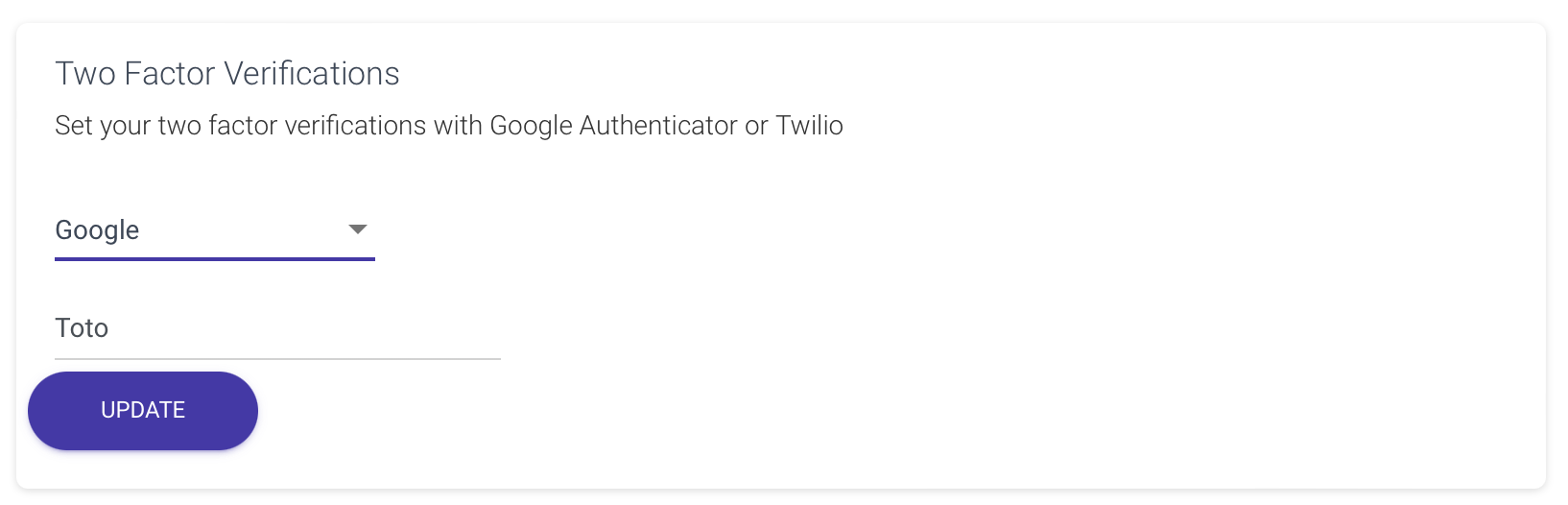
Inside the mobile app, when the user activates Google 2FA, a QR code and a secret key are displayed. To initialize the 2FA, the user simply scans the QR code using the Google Authenticator application.

Phone Two Factor Verification #
The Phone two-factor verification employs a 6-digit SMS code sent to the user’s phone via the CoSync Auth application, serving as a means to verify their identity. To utilize this authentication method, the developer must supply a Twilio account SID, a Twilio Auth Token, and a Twilio phone number designated for sending the SMS messages. Access to these keys is available through the developer’s Twilio account dashboard.
It is crucial to note that unlike the free Google Authenticator, the Phone two-factor verification system incurs costs, as the developer’s Twilio account will be charged for each message sent. For applications with a substantial user base, Twilio expenses can escalate rapidly, warranting caution in this regard. Nonetheless, this authentication method is typically preferred by security-conscious users who expect this added layer of protection.
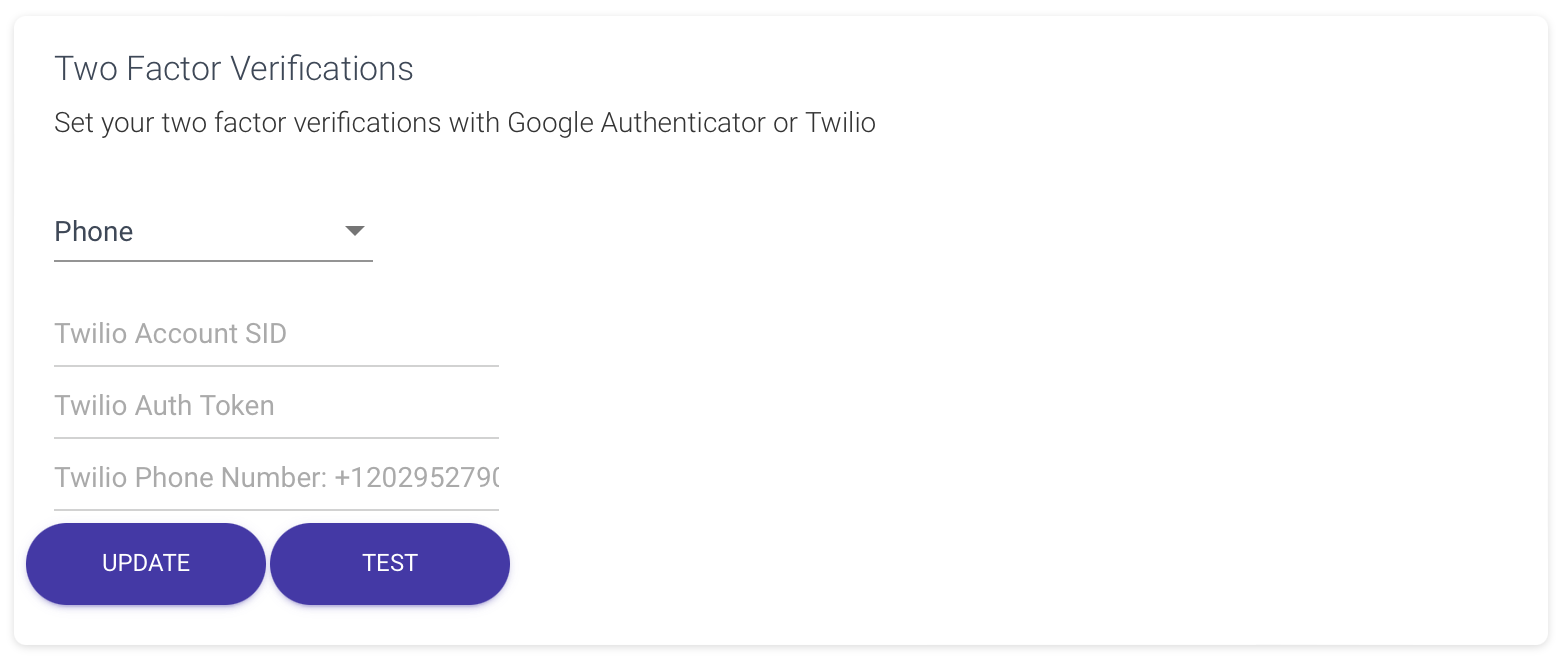
When implementing Phone 2FA, the developer’s application usually mandates the user to furnish a distinct phone number, which must also undergo verification. The CoSync Auth authentication REST API furnishes appropriate functions to facilitate this process seamlessly. After successfully verifying the user’s phone number, they can proceed to activate Phone 2FA for their account. Once enabled, every time the user logs in, a six-digit SMS message will be sent as an additional security measure.
To accommodate this scenario, the app developer must integrate extra user interface components, ensuring smooth handling of the Phone 2FA setup and verification process.