How to retreive application keys
The Keys tab contains RSA public key used by MongoDB Realm to verify the authenticity of the CosyncJWT signing authority and the app token used to access the Cosync REST Service API.
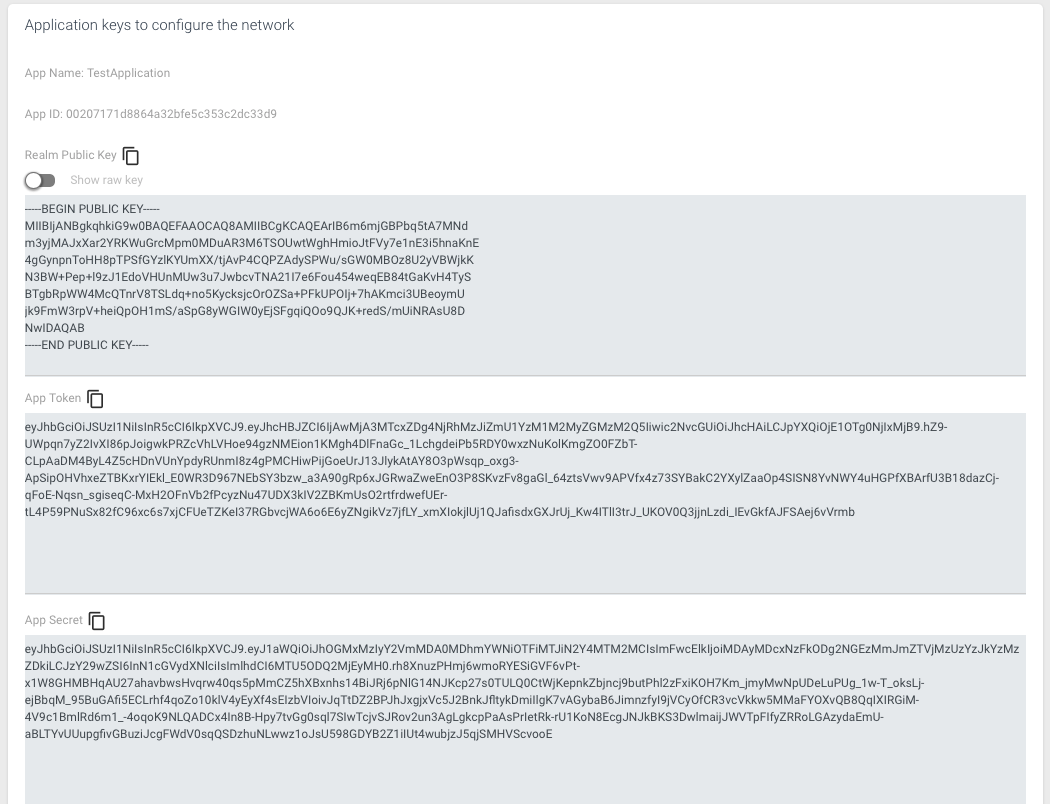
The Realm Public Key field contains the RSA public key associated with the hidden private key for the application. This key is presented in the following format:
-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEArIB6m6mjGBPbq5tA7MNd
m3yjMAJxXar2YRKWuGrcMpm0MDuAR3M6TSOUwtWghHmioJtFVy7e1nE3i5hnaKnE
4gGynpnToHH8pTPSfGYzlKYUmXX/tjAvP4CQPZAdySPWu/sGW0MBOz8U2yVBWjkK
N3BW+Pep+l9zJ1EdoVHUnMUw3u7JwbcvTNA21I7e6Fou454weqEB84tGaKvH4TyS
BTgbRpWW4McQTnrV8TSLdq+no5KycksjcOrOZSa+PFkUPOIj+7hAKmci3UBeoymU
jk9FmW3rpV+heiQpOH1mS/aSpG8yWGIW0yEjSFgqiQOo9QJK+redS/mUiNRAsU8D
NwIDAQAB
-----END PUBLIC KEY-----
It is this public key, presented in the BEGIN PUBLIC KEY format that is copied and inserted in the JWT Provider tab of the associated MongoDB Realm Application, in order to turn on JWT authentication.
To get a raw key version of this RSA public key, you can click on the Show Raw Key toggle and get the following format:
LS0tLS1CRUdJTiBQVUJMSUMgS0VZLS0tLS0KTUlJQklqQU5CZ2txaGtpRzl3MEJBUUVGQUFPQ0FROEFNSUlCQ2dLQ0FRRUFySUI2bTZtakdCUGJxNXRBN01OZAptM3lqTUFKeFhhcjJZUktXdUdyY01wbTBNRHVBUjNNNlRTT1V3dFdnaEhtaW9KdEZWeTdlMW5FM2k1aG5hS25FCjRnR3lucG5Ub0hIOHBUUFNmR1l6bEtZVW1YWC90akF2UDRDUVBaQWR5U1BXdS9zR1cwTUJPejhVMnlWQldqa0sKTjNCVytQZXArbDl6SjFFZG9WSFVuTVV3M3U3SndiY3ZUTkEyMUk3ZTZGb3U0NTR3ZXFFQjg0dEdhS3ZINFR5UwpCVGdiUnBXVzRNY1FUbnJWOFRTTGRxK25vNUt5Y2tzamNPck9aU2ErUEZrVVBPSWorN2hBS21jaTNVQmVveW1VCmprOUZtVzNycFYraGVpUXBPSDFtUy9hU3BHOHlXR0lXMHlFalNGZ3FpUU9vOVFKSytyZWRTL21VaU5SQXNVOEQKTndJREFRQUIKLS0tLS1FTkQgUFVCTElDIEtFWS0tLS0t
Sometimes the developer needs a raw key when calling a cryptographic library from within their code.
The App Token should also be copied and pasted into the constants file of the applications code. It is this JWT token that is used by the CosyncJWT REST API to authenticate the calling application.
eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9.eyJhcHBJZCI6IjAwMjA3MTcxZDg4NjRhMzJiZmU1YzM1M2MyZGMzM2Q5Iiwic2NvcGUiOiJhcHAiLCJpYXQiOjE1OTg0NjIxMjB9.hZ9-UWpqn7yZ2IvXI86pJoigwkPRZcVhLVHoe94gzNMEion1KMgh4DlFnaGc_1LchgdeiPb5RDY0wxzNuKolKmgZO0FZbT-CLpAaDM4ByL4Z5cHDnVUnYpdyRUnmI8z4gPMCHiwPijGoeUrJ13JlykAtAY8O3pWsqp_oxg3-ApSipOHVhxeZTBKxrYIEkl_E0WR3D967NEbSY3bzw_a3A90gRp6xJGRwaZweEnO3P8SKvzFv8gaGl_64ztsVwv9APVfx4z73SYBakC2YXylZaaOp4SISN8YvNWY4uHGPfXBArfU3B18dazCj-qFoE-Nqsn_sgiseqC-MxH2OFnVb2fPcyzNu47UDX3kIV2ZBKmUsO2rtfrdwefUEr-tL4P59PNuSx82fC96xc6s7xjCFUeTZKeI37RGbvcjWA6o6E6yZNgikVz7jfLY_xmXIokjlUj1QJafisdxGXJrUj_Kw4ITlI3trJ_UKOV0Q3jjnLzdi_IEvGkfAJFSAej6vVrmb
If you go to the website (jwt.io), you can actually decode the JWT App Token. The header contains
{
"alg": "RS256",
"typ": "JWT"
}
while the payload contains
{
"aud": "junctiontest1-bbeas",
"sub": "rckrueger@gmail.com",
"exp": 1598421554,
"email": "rckrueger@gmail.com",
"user_data": {
"name": {
"first": "Richard",
"last": "Krueger"
}
},
"iat": 1598385554
}
The aud field specifies the audience of the JWT token, in this case the MongoDB Realm Application Id. The sub field specific the subject of the JWT token, in this case the email of the user that was authenticated. The exp provides an expiration date for the token. The email and user_data properties are the metadata attached to the JWT token that contain user information. The format of this metadata is specified in the Application Settings tab.
Since this is signed with the CosyncJWT private key, it is near impossible to counterfeit.